
views
X
Research source
These codes can also help messages get past censors in more serious situations. Knowing how to create, write, and send an encoded message using constrained language can help get your messages out undetected. Learning a few different constrained language codes can help your messages become even more secure.
Building an Acrostic Code

Think of what you want to encode. Before you can create a coded message, you will need to think of the message itself. You can encode any word or phrase using an acrostic code. However, you should try to keep your messages short. Longer messages can be difficult to encode and may be noticed by people that shouldn't see them. For example, you might want to hide a message like “HELP IN DANGER” You would likely want to avoid a message like “PLEASE HELP ME I AM IN DANGER” because it's too long.

Break the word or phrase down into letters. Building an acrostic will require you to break down each word into its individual letters. These letters will be inserted into a larger body of text. It's important that you use each letter of your phrase or word in the acrostic code. If you wanted to hide the word “HELP”, you would need to use H, E, L, and P in your message. Make sure you don't miss any letters, as this can change the code. For example, missing the letter L in “HELP” would result in the code reading “HEP”.

Write a sentence for each letter. Now that you have each letter of your word ready, you can begin building the code. Every letter will have its own sentence written after it. The code will be revealed by reading each first letter of every sentence. Make sure each letter is included in the document you are creating to ensure the code will be readable. As an example, imagine that you are trying to encode the word “HELP”. Your first sentence would have to start with the letter H. “How is everyone at home?” would be a good choice. The next sentence would need to start with the letter E. “Everything still going well in town?” could be used in this case. Continue in this way until the message is fully encoded. It's important that your sentences and message don't draw attention to the encoded message. Keep your tone and content neutral and natural.

Check your code. Complete the acrostic code and double-check it. You will want to make sure that each letter of your original phrase or word is included. Every sentence in your document should start with a letter from your original message. If you read the first letter of each sentence, you should find your original message. If you missed any letters, add them to your encoded message to make sure it's readable. Make sure you didn't add any sentences that aren't part of the code. This could change the meaning of the original message you were trying to encode. “How is everyone at home? Everything still good? Looking forward to coming back. Please take care of my dog until then!” would be an example of encoding the word “HELP” using the acrostic method.
Making a Code with Your Keyboard

Consider which word you want to encode. Before you can use this method to create a coded message, you'll need to know what you want to encode. You can choose almost any word you might want. However, it's a good idea to favor shorter messages, as longer codes may be more difficult to create.

Focus on key-rows. The keyboard code method works by using one row of keys at a time. The message itself is spelled out using letters from different rows on the keyboard. These different letters will build the message and keep it hidden amongst seemingly normal words. Check out some of these examples to get a good understanding of the keyboard code: There are three rows on the keyboard, one starting with Q, the next starting with A and the last starting with Z. You will need to think of words that use only one row of letters, with the exception of the letter you are using to build your code. You will spell out your code one letter at a time, hiding it in another word.

Think of words with exceptional letters. This method works by spelling a word with one row of keys, with only the coded letter being on a different row. Words that have this quality in your document will be focused on, taking the odd letter from each code word to rebuild your original message. To get a better understanding of how this works, check out these examples: “Terra” would hide the letter A. T, E and R are all in the top row of the keyboard while the letter A is in the second row. Because letter A isn't part of the row the other letters are, it stands out and is read as part of the coded message. “Rag” “art” “now” would hide the code word RAN.

Spell your code out with odd letters. Once you have some words to use for this method, you can encode your entire message using the keyboard code. It's important to remember that you don't need to use every word to build your code. Only words with an odd letter out of one row will be read as part of the code. Make sure your key codewords correctly spell out your message before sending it out. “Don't rag on me so much. Writing things is an art. Now, send me another message.” would encode the word RAN. The keywords are the rug, art, and now and they hide the letters r, a, and n. Only the words using the keyboard code will be decoded. Not every word will be part of the code. In fact, many words in your document will not be used as part of the code. Be careful not to accidentally include words that might be part of the code. Use only words that are made on one row of keys or all three, if they aren't part of the code.
Using Spelling Errors to Send a Code

Consider a word you want to encode. The first step that you will need to take is to think of a word or phrase that you want to encode. This keyword or phrase will be one that you need to keep secret, encoding it in a larger document using spelling errors. Anyone reviewing your message will likely overlook simple spelling errors and let your message slip through. Try to keep your message simple and short. “SEND HELP” would be a good example. Messages such as “PLEASE HELP ME I'M IN DANGER” might be too long or too difficult to hide using the spelling error code.

Start writing. Write your letter as you normally would, using your natural writing style and voice. It's important to remember that you will need to spell every regular word normally to make this method work. Any actual spelling errors could change your message. Much of the letter you send using this method will look completely normal.

Include misspellings to hide your message. You will need to hide your message by spelling it out using spelling errors. These incorrect letters will be read one-by-one, building your message and deciphering the code. Think about how you can spell words in your message incorrectly to hide your message. Imagine you want to hide the word “RUN” in your document. “Terific! Nevur have been there. Annother day perhaps?” would encode the word RUN using spelling errors. A letter R is missing from "terrific", the letter U is used instead of E in "never" and the word "another" has an extra letter N. Try to space out your spelling errors. Make them look like actual mistakes. Don't randomly place letters that wouldn't naturally be mistaken. For example, “I zaw a ghost” would likely stand out too much if you're trying to include the letter Z in your message.

Check your code. Before you send your code off, make sure your message is properly encoded. Each spelling error should build your coded message and allow the recipient to decipher the code. If everything is in order, you can send your message off and await a reply. If you missed any letters that make up your code, go back and add them in. It's important that you spell everything else correctly. Accidental misspellings will change the message.
Building A Stronger Code
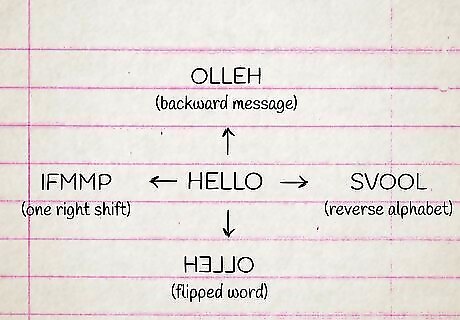
Use multiple methods. You can try using multiple coding methods to hide different messages in your note. These can act as added layers of security, stopping anyone from discovering sensitive parts of your message. Try combining a few of these coding methods in your documents or letters to help keep your messages secret. You can combine ciphers with other code methods to increase the security of your message. You might use the acrostic method to hint at the real message which was encoded using the spelling error code. You could try writing "SPELLING ERRORS" with an acrostic code to indicate another message using the spelling error code. You could try encoding half the message with the keyboard method and the other with the acrostic method. Try encoding the first letter of a word with one code method and the next letter with another method. Keep alternating codes, using both coding methods, to build a more secure message.

Work with a friend to breach each other's codes. Spending some time breaking coded messages can give you a better understanding of how codes work. You'll be able to learn what works well or how someone might be able to break your own codes. If a friend breaks your code, that means it's too easy to guess. Learn from your mistakes and create a more difficult code.

Keep the message natural. Whenever you are encoding a message into a larger document, it's important that you keep your overall document natural in tone and writing. Any irregularities could draw attention to your message, causing your code to be broken and intercepted. It's important that your messages always look and read as if they were nothing special. Ask someone to read over your message and note anything that sticks out. If something sticks out, your tone wasn't neutral enough.

Reply using the same code. If you receive a message using a certain code, you should reply using that same code. Sending a different code might make the original sender think that you missed the message and may cause them to miss your own message. Always communicate using the established code method to ensure the messages are passed clearly. Ciphers will require you and a contact to use the same cipher.

Practice codes beforehand. Coming up with a coded message system after it becomes necessary can be difficult. For this reason, it's a good idea to establish which codes you will use and how they will be used before it becomes an issue. This will allow you to more easily encode, decode, and return secret messages in any situation. Some codes require you to share them with a friend. For example, if you and a friend were using a cipher wheel, you would both need to know the what cipher you are using to decode the message. Get in plenty of practice using your method of choice. You and a friend can practice both sending and receiving coded messages to each other.



















Comments
0 comment