
views
Samsung reportedly hosted a whole bunch of crucial data, including app source codes, secret keys, authorisation credentials, usage logs and analytics, on a development lab hosted on a company-owned domain, without proper security measures. The data, which was hosted in a GitLab folder using the domain ‘Vandev Lab’, reportedly included critical information such as full access to the AWS account being used by the developers, and once access was procured, contained source codes of apps already published on the Google Play Store.
As reported by TechCrunch, security researcher Mossab Hussein discovered the GitLab instance, which was being used by developers within the Samsung ecosystem to share data and codes of numerous Samsung projects and services. However, the worrying bit here is that a bunch of these codes were pertaining to public-facing services, and reportedly included highly sensitive code material for Samsung SmartThings and Bixby. The GitLab repository in which all the code was hosted, was set to ‘public’, with no proper password protection. This, in turn, would have reported almost anyone to take a look at it, and download the source code dumps.
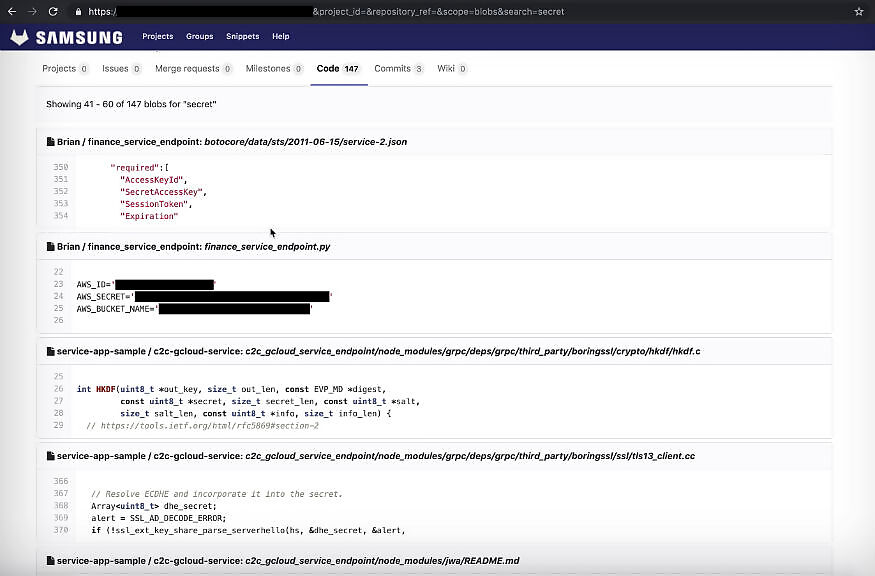
This could have further led to a possible instance where malicious users could have injected any form of malware, under pretext of official code. As Hussein discovered, the repository also had private GitLab tokens of multiple users stored in plaintext, which in turn allowed him access to up to 135 projects, with many of them being private, and in turn, possibly still under internal testing and potentially capable of developing into public services one day.
Hussein even gained access to a token that allowed him permission to all 135 of these projects, thereby leaving the Samsung data in his mercy. Any potential hacker could easily install malicious codes into this code base, and if downloaded by millions of users across the world, could lead to data breaches of devastating consequences. In response, Samsung spokesperson Zach Dugan told TechCrunch that the company is investigating the entire GitLab instance, and is “yet to find evidence that any external access occurred.” The company has already revoked the AWS credentials on the platform, but are yet to confirm if the remaining keys and certificates have been revoked as well.
Samsung has stated that the entire pool of data, however sensitive in nature, did not concern any already-published applications, but nevertheless updated the Samsung SmartThings app on Android stores already. Hussein, on this note, has claimed to possess evidence that the codes did affect public apps. It remains to be seen if this develops into a data breach issue, or if Samsung gets away with a major gaffe for one of the world’s largest technology and electronics makers.

















Comments
0 comment